Securing your AWS (Amazon Web Services) environment and ensuring compliance with industry standards are critical aspects of maintaining a robust and trusted cloud infrastructure. By implementing best practices for AWS cloud security and compliance, you can enhance the protection of your data, prevent unauthorized access, and meet regulatory requirements.
This blog highlights some critical areas to consider. From implementing strong identity and access management controls to employing encryption techniques and continuously monitoring your environment, these best practices will help you establish a secure and compliant AWS environment.
Follow these guidelines to build a foundation of trust and confidence in your cloud infrastructure while safeguarding your valuable assets and sensitive information.
But first, let’s demystify how AWS cloud security works.
Demystifying the Operation of AWS Cloud Security
AWS operates on the foundation of a shared responsibility model, where AWS assumes the responsibility for security “of” the cloud infrastructure, while AWS customers are accountable for security “in” the cloud. AWS places a strong emphasis on safeguarding their infrastructure, encompassing computing, AWS storage types, networking, and database services, to defend against intrusions and protect their global network of physical servers.
The customer’s role commences with the secure utilization of AWS. While AWS provides features like multifactor authentication (MFA) as a service, it is the customer’s responsibility to activate and implement MFA. Consequently, any unmanaged services or resources fall under the purview of the customer, who must undertake the necessary security measures to ensure their protection.
Essential Best Practices for AWS Cloud Security
Ensuring the Security of Administrator Credentials
Administering cloud environments requires diligent attention to the security of administrator credentials. By implementing robust practices and maintaining a proactive approach, organizations can significantly enhance the protection of their administrator accounts.
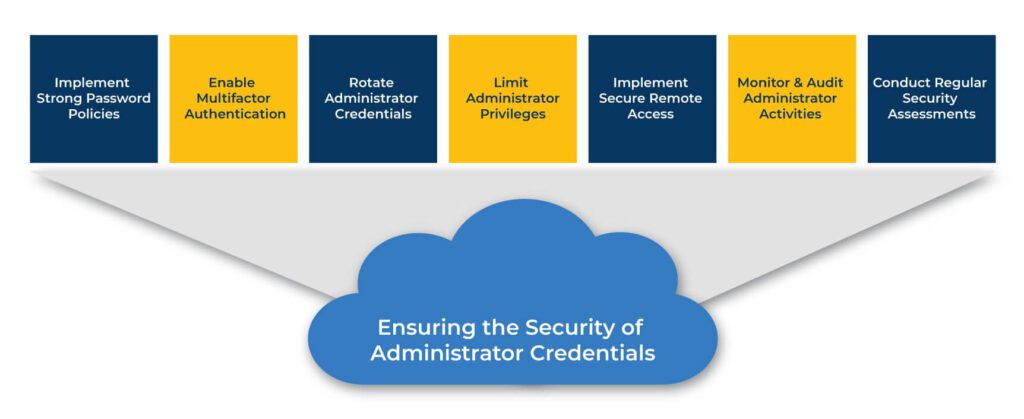
Here are some key considerations for conducting due diligence on administrator credentials:
Implement Strong Password Policies
Establish stringent password requirements for administrator accounts, including the use of complex and unique passwords. Encourage regular password updates and discourage the reuse of passwords across multiple accounts or services.
Enable Multifactor Authentication (MFA)
Implement MFA for administrator accounts to add an extra layer of security. By requiring an additional verification factor, such as a mobile app or hardware token, MFA helps prevent unauthorized access even if the password is compromised.
Regularly Rotate Administrator Credentials
Regularly change and rotate administrator credentials to reduce the risk of unauthorized access. Implement a password rotation policy that mandates periodic changes, ensuring that old credentials are invalidated and no longer usable.
Limit Administrator Privileges
Follow the principle of least privilege by assigning administrator privileges only to individuals who require them for their specific roles and responsibilities. Restricting privileges helps minimize the impact of a compromised administrator account.
Implement Secure Remote Access
Utilize secure remote access methods, such as Virtual Private Networks (VPNs) or bastion hosts, to protect administrator credentials during remote administration. You should also encrypt network traffic to prevent unauthorized interception and eavesdropping.
Monitor and Audit Administrator Activities
Another best practice is to implement robust monitoring and auditing mechanisms to track administrator activities. Regularly review logs and access records to detect any suspicious or unauthorized actions, allowing for timely response and investigation.
Conduct Regular Security Assessments
It is critical that you perform periodic security assessments and vulnerability scans to identify any potential weaknesses in administrator credentials. Moreover, you should address any identified vulnerabilities promptly and proactively to maintain a secure environment.
Best Practices to Secure AWS Network
The next step to manage is ensuring robust network security, which is vital for safeguarding your AWS cloud infrastructure. By implementing these best practices, you can strengthen your network security posture:
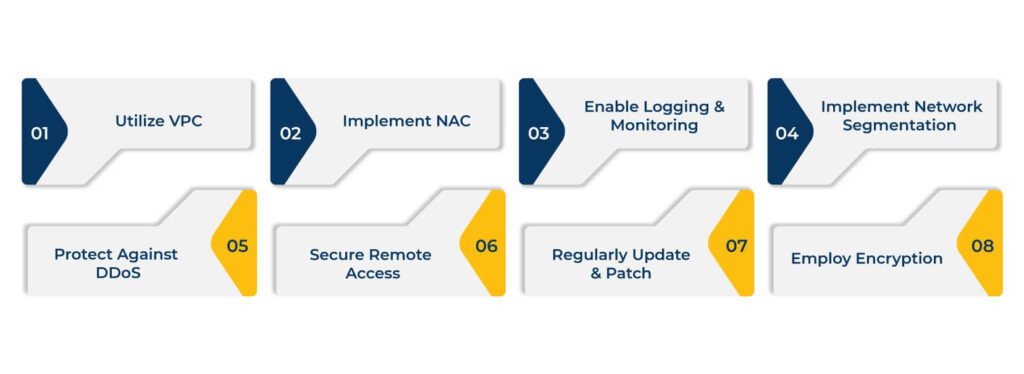
Utilize Virtual Private Cloud (VPC) Effectively
- Create separate VPCs for different environments (e.g., production, development, and testing).
- Segment your VPC using subnets and employ network access control lists (ACLs) for granular traffic control.
- Implement security groups to control inbound and outbound traffic at the instance level.
Implement Network Access Control
- Use AWS Security Groups to define allowed inbound and outbound traffic rules.
- Restrict access by configuring security group rules based on the principle of least privilege.
- Regularly review and update security group rules to ensure they align with current requirements.
Enable Logging and Monitoring
- Activate VPC Flow Logs to capture information about network traffic.
- Use AWS CloudTrail to log API activity and AWS network actions.
- Leverage AWS CloudWatch to set up alarms and monitor network-related metrics.
Implement Network Segmentation
- Divide your network into smaller subnets to isolate different components or tiers.
- Use separate subnets for public-facing and internal resources.
- Apply network access control lists (ACLs) to control traffic flow between subnets.
Protect Against Distributed Dtinyenial of Service (DDoS) Attacks
- Utilize AWS Shield, a managed DDoS protection service, to safeguard your applications.
- Consider using AWS WAF (Web Application Firewall) to protect against common web exploits.
- Configure DDoS protection settings on AWS Elastic Load Balancers.
Secure Remote Access
- Utilize AWS Virtual Private Network (VPN) or AWS Direct Connect for secure remote access.
- Implement strong authentication mechanisms such as multifactor authentication (MFA).
- Use secure protocols (e.g., SSH and HTTPS) for remote management and data transfer.
Regularly Update and Patch
- Keep your network infrastructure, including routers, switches, and firewalls, up to date with the latest security patches.
- Apply updates promptly to mitigate vulnerabilities and protect against known threats.
Employ Encryption
- Use Secure Sockets Layer/Transport Layer Security (SSL/TLS) to encrypt data in transit.
- Encrypt sensitive data at rest using AWS Key Management Service (KMS) or other encryption solutions.
- Enable encryption on AWS services such as Amazon S3, Amazon RDS, and Amazon EBS.
Best Practices to Secure AWS Data
Protecting data is of paramount importance in any cloud environment. Implementing the following AWS best practices for data security will help you maintain the confidentiality, integrity, and availability of your sensitive information:
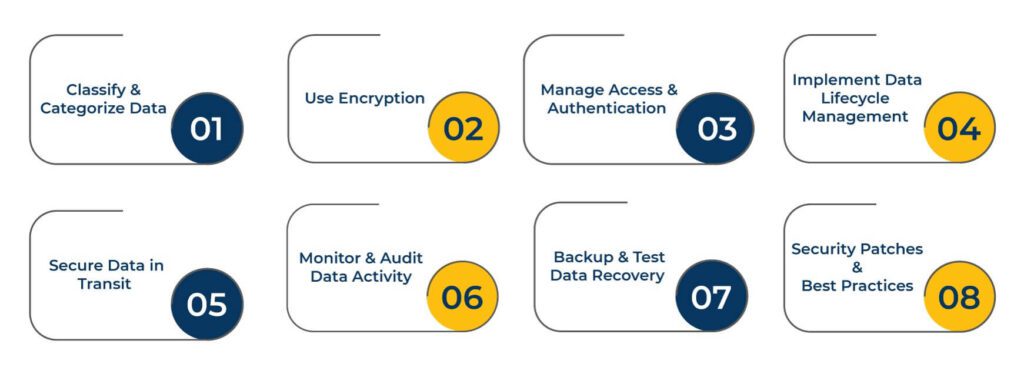
Classify and Categorize Data
- Understand the sensitivity and classification of your data.
- Apply appropriate security controls based on the data classification level.
- Implement data access controls and encryption based on data sensitivity.
Use Encryption
- Encrypt data at rest using AWS Key Management Service (KMS) or other encryption solutions.
- Implement encryption in transit using SSL/TLS protocols.
- Use AWS services like Amazon S3, Amazon RDS, and Amazon EBS with encryption enabled.
Manage Access and Authentication
- Utilize AWS Identity and Access Management (IAM) to manage user access and permissions.
- Follow the principle of least privilege, granting users only the necessary access rights.
- Implement MFA for enhanced user authentication.
Implement Data Lifecycle Management
- Define data retention policies and implement automated data deletion or archival processes.
- Regularly review and update data access permissions based on changing business needs.
- Consider using AWS services like Amazon S3 lifecycle policies for automated data management.
Secure Data in Transit
- Use Virtual Private Cloud (VPC) and private subnets for secure network communication.
- Implement secure protocols (e.g., HTTPS, SSL/TLS) for data transmission.
- Leverage AWS Direct Connect or AWS VPN for secure remote access to your data.
Monitor and Audit Data Activity
- Enable AWS CloudTrail to capture and log API activity related to your data.
- Implement logging and monitoring solutions to track data access and changes.
- Use AWS CloudWatch or third-party monitoring tools to set up alerts for suspicious activities.
Regularly Backup and Test Data Recovery
- Implement regular backups of critical data using AWS services like Amazon S3 or Amazon EBS.
- Test data recovery processes to ensure the ability to restore data when needed.
- Consider utilizing AWS Backup for centralized and automated data backup.
Stay Updated with Security Patches and Best Practices
- Keep your AWS services and underlying infrastructure up to date with the latest security patches.
- Follow AWS security advisories and best practices to address known vulnerabilities.
- Regularly assess your data security controls and adjust them based on emerging threats and industry standards.
Wrap Up
Cloud security is a vital element for businesses operating in cloud environments. And since AWS is a leading cloud service provider, these guidelines will surely help you secure your AWS cloud infrastructure.
If you need further assistance with securing your cloud setup, contact us at [email protected] for a free consultation session. Xavor is an AWS Partner and our DevOps & Cloud team would get in touch with you to see how our services can benefit you.












