Cloud computing has become a critical component of almost every organization’s IT infrastructure in the last few years. As companies store and process an increasing amount of data in the cloud, it has become crucial to ensure the security of cloud-based systems. AWS is one of the leading cloud computing service providers, offering a wide range of cloud-based services and products. This blog post will explore how you can enhance cloud security in Amazon Web Services (AWS).
AWS Security – A Shared Responsibility Model
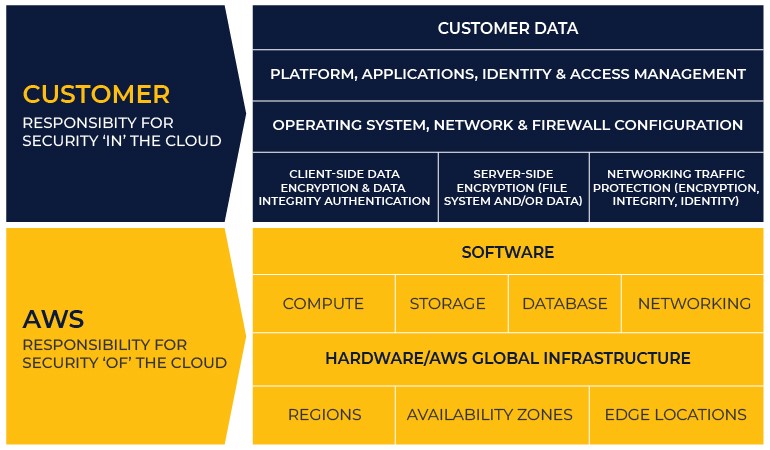
The AWS security and compliance model is a shared responsibility framework; it outlines the division of security responsibilities between AWS and its customers. It also helps define the areas where AWS is responsible for security and the areas where the customer is responsible for security. This shared responsibility model recognizes that security is a collective responsibility between the cloud service provider (AWS) and the customer using the AWS services.
Amazon differentiates the two types of responsibilities as security “of” the cloud vs. security “in” the cloud. We explain this differentiation below.
AWS – Security of the Cloud
Under the shared responsibility model, AWS takes responsibility for the security of the underlying cloud infrastructure, including the physical security of the data centers, networking hardware, the host operating system, and the hypervisor. AWS also manages the security of certain services and features such as computing, storage, database, and networking services.
Therefore, it significantly reduces the operational burden on the customer.
Customer – Security in the Cloud
On the other hand, an AWS customer’s responsibility depends on the services they use; these services then determine the configuration work that the customer must perform to fulfill their end of the shared responsibility model.
As such, AWS customers are tasked with securing their data, applications, guest operating systems, and other services that they deploy on the AWS infrastructure. This includes securing access to their AWS cloud computing, managing user access to their AWS resources, configuring their network, managing their firewall settings, and deploying security measures such as encryption, access control, and monitoring.
For example, suppose you want to use Amazon Elastic Compute Cloud (EC2), an infrastructure-as-a-service (IaaS). You will have to manage the guest operating system (security patches and updates) and the application or utilities you install on the instances. Moreover, you will also be responsible for configuring the AWS firewall on each instance.
Following a shared security framework helps you ensure the security of your systems, in addition to benefiting from the AWS-provided security measures.
Maximizing AWS Cloud Security
AWS provides a secure infrastructure for its customers to build and deploy their applications. It offers various security services and features, such as identity and access management (IAM), virtual private cloud (VPC), encryption, and monitoring. However, the responsibility for securing the customer’s applications and data rests with the customer.
International security standards provide us with a framework for designing, implementing, and managing a secure information system. By applying that knowledge and skills in AWS, you can enhance the security of your cloud-based systems.
Here are some steps and exercises you can undertake to bolster AWS cloud security:
1. Risk Management
A comprehensive approach to risk management includes identifying, assessing, and mitigating risks. AWS customers can use the standardized risk management framework to identify and assess the risks associated with their cloud-based systems.
AWS offers various security services and features, such as AWS Config, AWS CloudTrail, and Amazon Inspector, to help customers monitor their systems for security risks.
2. Identity and Access Management (IAM)
IAM is a critical component of AWS security. It enables customers to manage user access to AWS resources. You can use the knowledge and skills of security-certified professionals in identity and access management to design and implement secure IAM policies in AWS.
By applying standard IAM principles, organizations can ensure that only authorized users have access to their cloud-based systems.
3. Security Assessment and Testing
Security assessment and testing are vital for identifying vulnerabilities and weaknesses in cloud-based systems. It includes knowledge and skills in security assessment and testing, which you can utilize to design and implement effective security testing procedures in AWS.
Moreover, AWS offers various security testing services, such as Amazon Inspector, AWS Security Hub, and AWS Config Rules, that you can use to assess and test the security of cloud-based services.
4. Communication and Network Security
In-depth knowledge of network and communication security standards is very helpful for ensuring adequate network security on AWS (Amazon Web Services) platforms. To implement this knowledge for AWS network security, you must understand the AWS shared responsibility model and the security responsibilities shared between AWS and the customer.
Implementing security measures, such as network access control lists (ACLs), AWS Security Groups, and AWS Web Application Firewall (WAF), encryption, and monitoring network traffic can help secure communication on AWS.
5. Security Operations
Security operations are critical for ensuring the security of cloud-based systems. It provides knowledge and skills in security operations, which can be used to design and implement effective security operations procedures in AWS.
AWS offers various security operations services, such as AWS GuardDuty, Amazon Macie, and AWS WAF, that can be used to monitor and manage the security of cloud-based systems.
Conclusion
To sum it up, you can design, implement, and manage secure cloud-based systems in AWS by leveraging the knowledge and skills of cloud security experts. AWS offers various security services and features that can be used to implement standard security principles. However, it is essential to remember that AWS security is a shared responsibility model; AWS is responsible for the security of the underlying infrastructure, while the customer is responsible for the security of their applications and data.
Xavor offers AWS services and solutions to help you improve your cloud environment’s security and performance. Drop us a line today at [email protected] to learn how we can help you unlock cloud computing’s true potential.












