Infrastructure as Code
Infrastructure as Code (IaC) enables developers to define infrastructure in a way that automates, accelerates, and repeats provisioning. It’s an integral part of Agile and DevOps techniques, like continuous integration, continuous deployment, and version control.
Terraform Introduction
Do you have questions like what is terraform provisioning in Azure? Are you keen to learn about resource provisioning and the relationship between Terraform and Azure? Do you know how the Terraform Azure resource group came into being? You have landed in the right place. You can construct, modify, and version infrastructure securely and effectively using HashiCorp Terraform. It is an open-source platform that handles Infrastructure as Code. The declarative, proprietary language known as HashiCorp Configuration Language (HCL) is used to create Terraform configurations (HCL). It examines every resource in the directory marked with an a.tf extension before carrying out the configuration. For terraform provisioning, you will need help from Azure resource provisioning
Terraform Provisions Immutable Infrastructure
Terraform provides an execution plan before deployment that explains what it will do and seeks your permission before making any infrastructure modifications. These provisioners help in executing scripts or in some cases shell commands over a local machine. They sometimes do on a remote machine where it involves addition or deletion of a resource.
Create a base Terraform configuration file
provider “azurerm” {
version = “~>2.0”
features {}
}
resource “azurerm_resource_group” “rg” {
name = “<resource_group >”
location = “<East US>”
}
Initializing Terraform
terraform init
Creating Terraform Plan
terraform plan
Terraform Apply/Run
terraform apply
Azure Portal: Resource Group
- Create Terraform Configuration file(provider.tf)
- Set our Terraform Plan
- Execute “Terraform apply” to run your Terraform Plan
- You have access to Azure Resource Provisioning Group automatically via Terraform
Terraform Important Concepts
Terraform Language
You can declare the resources for infrastructure using HCL. Terraform provisioning requires provisioning resources. The arguments and block syntax constructs form the foundation of the Terraform language syntax.
A block has labels and a type. How many labels must come after a block type is specified for each block type?
<BLOCK TYPE> “<BLOCK LABEL>” “<BLOCK LABEL>”
{
<IDENTIFIER> = <EXPRESSION> # Argument
}
example: A resource block specifies a given type of resource
(“azurerm_resource_group”) with a given local name (“vnet_main”).
resource <resource type> <local name>
resource “azurerm_resource_group” “vnet_main”
{
name = var.resource_group_name
location = var.location
}
Terraform providers
Azure Resource Provisioning types or provisioning resources are implemented via plugins called Terraform providers. Providers include information that enables clients of Terraform to connect to the platform. You can locate providers for the cloud services and platforms you employ, include them in your configuration, and then use their resources to provision infrastructure.
Example Providers:
- Azure: azurerm, azuread
- AWS: aws
- Google: google
Terraform Modules
Terraform modules are reusable containers. Technically, any collection of Terraform configuration files in a folder is a module because a module is simply a collection of related.tf and/or.tf.json files are maintained together in a directory. The term “child module” is frequently used to describe a module that has been called by another module.
Terraform can load modules from a private or public registry. The Terraform Registry is a good illustration of a public registry. It includes products created by the Terraform community members, third-party providers, and HashiCorp. Moreover, Module Blocks dictate how to pronounce or call a child module from a parent module, encompassing essential syntax elements including, the utilization of meta-arguments, such as for_each.
Then comes the Module Sources that detail the acceptable paths, addresses, and URIs which are and could be employed in the source parameter within a module block.
The Meta-Arguments section provides documentation and records on special parameters applicable to every module. This includes information about providers, depends_on, count, and for_each.
Terraform Variables
Terraform supports the following kinds of variables or named values:
- Users can modify behavior without changing the source code by using input variables as parameters for a Terraform module.
- For a Terraform module, output values are similar to return values.
- A practical feature for giving an expression a short name is called local values.
Please visit the documentation for more details.
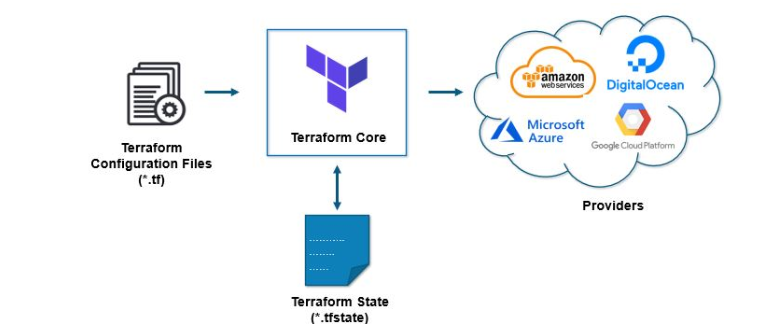
Terraform State
Terraform state is used by tf to track metadata and map real-world resources to your configuration. uses the state to keep track of connections between resources declared in your configuration and objects in a remote system. It is automatically saved as a local file with the name terraform. tfstat
Deployment Using Terraform is Essentially a 4-Step Process
- Terraform init
- Terraform Plan
- Terraform Apply
Brief Explanation
For terraform provisioning, you have to configure the file and add all the details, including the resource group name, container, storage account name, and key name. If not, you can choose to insert these details directly using the “terraform init” command.
terraform
{
backend “azurerm”
{
resource_group_name = “resource grp name”
storage_account_name = “storage account name
container_name = “azure blob container name”
key = “tf state file ex: dev.terraform.tfstate”
}
}
Step 1
To prepare a directory, initialization carries out several operations, such as accessing the preset backend state, downloading and installing provider plugins, and downloading modules.
terraform init
Step 2
For terraform provisioning, you must give Terraform the necessary information so that it can connect to your cloud subscription before continuing. There are several ways you can handle this. We will locally authenticate Terraform for this demonstration using the Azure CI CD Pipeline. Just use your machine’s Azure CLI to log in. This will save your login information on your work computer, where Terraform can pick it up immediately.
az login
Step 3
After initialization, you are prepared to use the terraform plan command to generate an execution plan. To construct the configuration given in your configuration files, it analyses each Terraform configuration file and determines what steps must be taken. Before making any modifications to actual resources, this pattern enables you to check that the execution plan corresponds to your expectations.
terraform plan -out vnet.tfplan
Step 4
In this step, we will apply this configuration. The information created as part of the plan will be carried out using Terraform apply.
terraform apply vnet.tfplan
Terraform Destroy
The “terraform destroy” command makes it simple to eliminate all remote objects controlled by a specific Terraform configuration. You have to make a plan first, and then destroy in the next step to destroy resources.
terraform destroy
Conclusion
Terraform provisioning features a template-based configuration file syntax, allowing you to automate the configuration and deployment of Azure app resources. You may reduce deployment and testing expenses by automating the creation and administration of infrastructure. A company’s infrastructure setup for IaC in the cloud and on-premises is automated via Terraform.
If you need further help with your Azure Resource Provisioning using Terraform, azure infrastructure as code Terraform, and Terraforming Azure then contact us at [email protected]. Our team would love to facilitate you!
FAQs
Yes, Terraform can be used seamlessly with Azure, offering a robust infrastructure-as-code solution for managing Azure resources efficiently.
Bicep and Terraform serve similar purposes, but the choice depends on preference. Some find Bicep, Azure’s DSL, more concise for Azure-specific deployments, while others prefer Terraform’s broader multi-cloud support.
To use an existing Azure resource in Terraform, you can import it using the Terraform import command, specifying the resource type and its identifier.
To deploy a resource group in Azure with Terraform, create a Terraform script defining the resource group and associated resources, then execute Terraform and apply it to provision them.
One weakness of Terraform is its potential learning curve for beginners. The complexity of its HashiCorp Configuration Language (HCL) may pose initial challenges.
Terraform and Kubernetes serve different purposes. Terraform focuses on infrastructure provisioning, while Kubernetes is a container orchestration platform. They are often used together to manage both infrastructure and containerized applications.